Cryptography is a science of encrypting information securely and privately such that it cannot be intercepted by any third parties. Cryptography has made it possible for us to keep our data and information secure no wonder it is our computer, smart devices or even the internet with processes such as Hashing, Encryption and Steganography.
Some might not know, but Cryptography is protecting the Internet and the virtual world.
The Basic of Cryptography
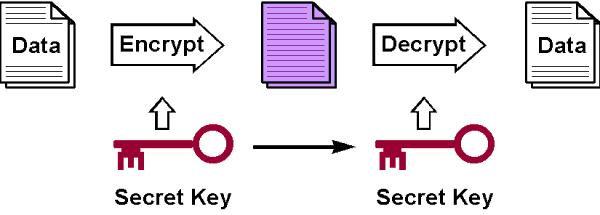
Cryptography is based on the backbone of encryption and decryption. Encryption means to convert data in some unreadable form, and decryption is the vice versa. The encryption and decryption works on one extra information is known as ‘key’, and based on key there can be different types of the decryption key.
Next, an important concern in cryptography is authenticity that ensures that the information over transmission was successfully delivered to the intended person, meaning, authenticity ensures that the message intended for ‘X’ is received by ‘X’ and no one else.
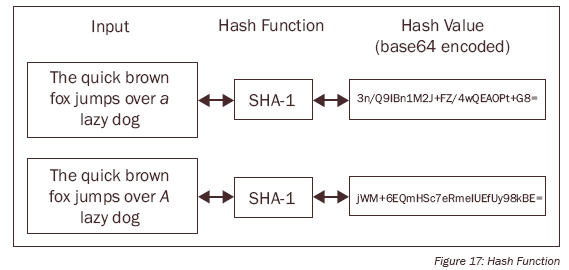
Integrity, which ensures that the message received by the intended user is not altered when transmitting through the communication medium with a cryptographic method known as hash.
Finally, Non Repudiation – there have been cases where the sender of the message has claimed that he never sent the message, and in such cases it was important to verify and as such digital signature came into existence.
Example:
Original Message: CRYPTOGRAPHY
Key: Next Adjecent Character, example – ‘A’ is replaced by ‘B’
Encrypted Message: DSZQUPHSBQIZ
Types of Cryptography
SECRET KEY CRYPTOGRAPHY
Here the same single key is used to encrypt the data from plain text and the same key is used by the end user for decrypting the encrypted message. This cryptographic method is a little insecure for the reason that the same key is used and in case of secret key distribution.
PUBLIC KEY CRYPTOGRAPHY
Public Key is more secure than Secret Key cryptography because here the plain text is encrypted using public key that is revealed to everyone you are communicating and the private key is kept secret using which one can decrypt message the final end.
HASH CRYPTOGRAPHY
Hash ensures message integrity that makes use of a hash function to compute one hash key of fixed length from the plain text. Basically, hashing ensure message integrity from alteration, compromising or other malicious activities.
As the adages goes, “Cryptography is the essential building block of independence for organizations of the Internet, just like armies are the essential building blocks of states, because otherwise one state just takes over another.” – Julian Assange